How does ETC come under a 51% attack two times in less than a week and this is the third time they have been in the bullseye. We are going to talk a little bit on what we first saw during the weekend as well as what we caught while renting hash during the same time as the first attack happened. A huge thank you to everyone in our discord for bringing this to our attention. We also want to thank BBT for bringing the actual attack to light via twitter so we could really start digging in!
Check out cointelegraph.com for their latest article as it breaks down a little more on how much was actually taken. This was not just some large farm some where loosing their internet like Ethereum Classic would like us all to think. What we mean by that is everyone was talking about a “reorganization” of the ETC chain… anyone who knows anything about mining is once someone “reorganizes the chain” that is an 51% attack on the network. Below is our first video when everyone was talking about how it was just some one who lost their internet.
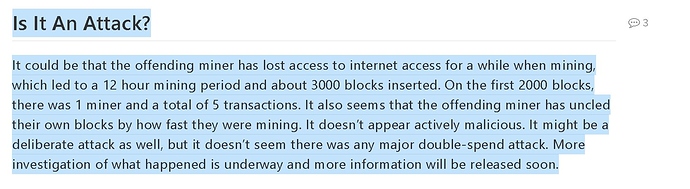
Once again a huge thank you to DOugy and EXLO from discord for first bringing this to our attention. We did a little digging shortly after finding out about this. This is one of the first articles we found talking about how they did not feel it was “malicious”. You can check that article out here at hackmd.io.
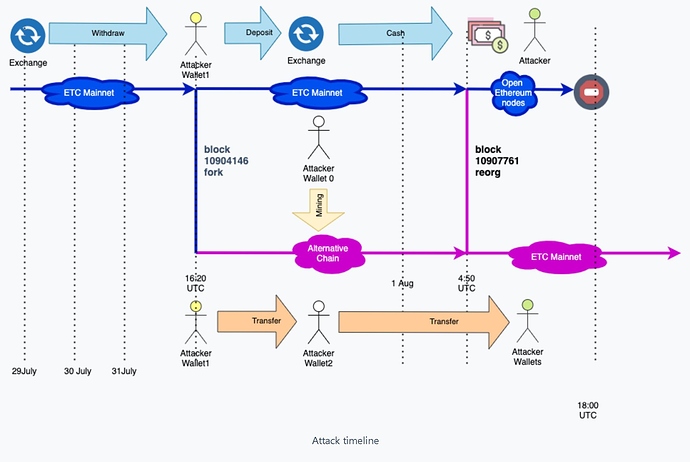
Things started to make much more sense catching a tweet from Carter (BBT) that had a link to blog.bitquery.io which really breaks things down even more. It is quite obvious especially since there was just a second attack that this had been planned and though of for quite some time.
It did not take us long to get our follow up video out discussing even more what information has come to the front of this attack on ETC. We had actually been using the service miningrigrentals.com doing some solo ethereum testing and we found some very interesting things.
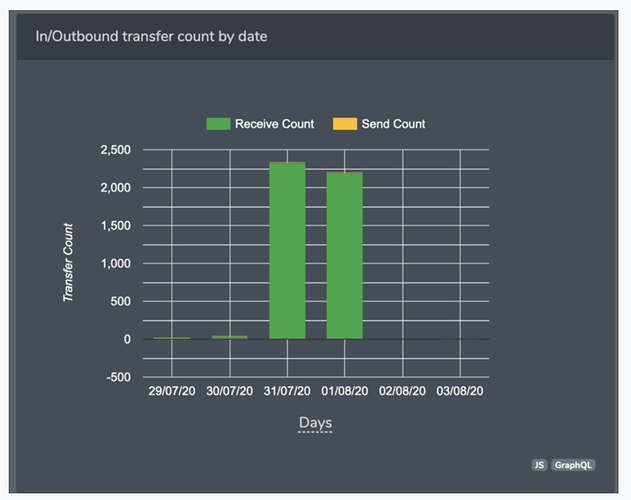
How did they get this attack executed? You can see in the stat below that if it was a “normal” miner there would be transactions or block rewards before and after the attack.
We were using the service miningrigrentals.com during this time. We had issues with a rig not hashing properly. It appeared this rig would come online and go offline for lenghts of time with a huge ramp towards the end. We don’t believe the rig owner was giving us the issues we feel that with serves like NH and MRR it is easy to “double dip” so to say. Sell your hash for more money and jump from one renter to another. Now we can’t confirm this but we do discuss this in our video above. You need large amounts of hash to do a 51% attack. Typically unless you have a large farm you need to use a provider to get that much hash. I am just nynm and can not confirm this.
We just learned about the second attack not to long ago from coindesk. This is going to cause ETC some serious issues IMO and with the length of time confirmations which last we saw some exchanges were over 4k needed. Pair that with this not being the first time this network has been under attack. In January of 2019 the same type of 51% attack happened. You can see more about that attack at bravenewcoin.
What does this mean for ETHEREUM CLASSIC? I honestly have no opinion. I feel the network will probably get attacked again since it appears to be an easy target at the moment. Please let us know what you think. I will not be mining any ETC for the near future and wish you all the best if you are a bagholder. Remember DYOR.
Ever wondered what it takes to 51% attack your favorite network? Check out crypto51 and you can see how much hash is needed to to this. Please DO NOT TRY THIS. NOT RECOMMENDED
If you liked this and want to see more of what we do please heck out more videos and other content over at our YT channel.