KEY FEATURES:
You will receive the fastest speed in the mining pool if you use T-Rex. The T-Rex has one of the most affordable use rates. We just take 1% of your mining
time as a payment for most of the available algorithms. This takes no more than 15 minutes per day.
Ethash, Kawpaw, Octopus, Autolykos 2, Blade 3, MTP, Firopow, and Progpower are currently supported. You may also control
your miner from your browser, eliminating the need to glance at your terminal. On your local network, you can make the miner’s web page accessible.
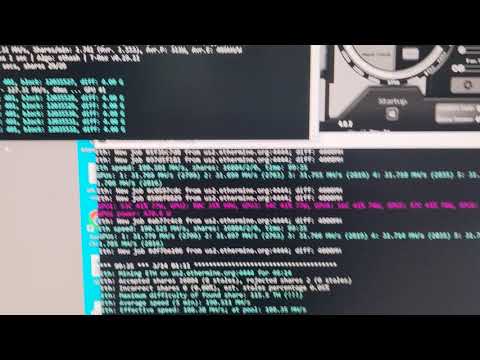
T-Rex is simple to incorporate into your applications or web services. All communication between the miner and your applications is done via
JSON structures and HTTP requests like “GET” and “POST.”
We don’t take a break from working on our miner. We want you to enjoy your time with T-Rex to the fullest.
Download
Latest release T-Rex v0.26.4
Windows: t-rex-0.26.4-win.zip
Linux: t-rex-0.26.4.tar.gz
Hive OS: t-rex-0.26.4-hiveos-custom.tar.gz
QUICK INSTALLATION GUIDE:
- Download the latest version of T-Rex Miner.
- Unzip the downloaded one .zip archive.
- You must create or change a file with the extension .but in the folder containing the miner. This can be done in any text editor (such as Notepad or Notepad ++).
- Replace the wallet address with your own. Example of configuration for Ethereum (ethermine):
Example of configuration for Ethereum (ethermine):
t-rex.exe -a ethash -o stratum+tcp://eu1.ethermine.org:4444 -u 0x1aa3e06C47caDEf96202D378aB7C407CF46A36A4 -p x -w rig0 pause
T-REX MINER VS PHOENIXMINER
On all fronts, holivars on the issue of “which miner is superior” are held on a regular basis: on YouTube, Reddit, Telegram chat rooms, and forums. “T-rex is the fastest, Phoenix overestimates the hash rate, Gminer will defeat them all, lolMiner is the most adequate, nothing beats TeamRedMiner, NBMiner can only be comprehended by the Chinese,” and so on.
Is T-Rex Miner better than Phoenix miner for gtx 1660 super mining ethereum? 31.8mh/s vs 31.7mh/s:
ANTIVIRUS ALERTS:
The binaries are packed using third-party software that mutilates the original machine code to shield the miner from reverse engineering assaults. As a result, some anti-virus engines can detect signatures in the executable file that are identical to those of real viruses that are protected by the same packer. In any event, bitcoin miners should not be used on computers that store sensitive information (wallets, passwords, etc.).